thick client application security testing tutorial|damn vulnerable thick client application : ODM This repository serves as a guide for understanding and addressing these challenges, covering various aspects of thick client penetration testing such as information gathering, traffic . Resultado da The technical storage or access is strictly necessary for the legitimate purpose of enabling the use of a specific service explicitly requested by the subscriber or user, or for the sole purpose of carrying out the transmission of a communication over an electronic communications network.
{plog:ftitle_list}
Utilizador - Jogos Santa Casa - Últimos Resultados - Totoloto
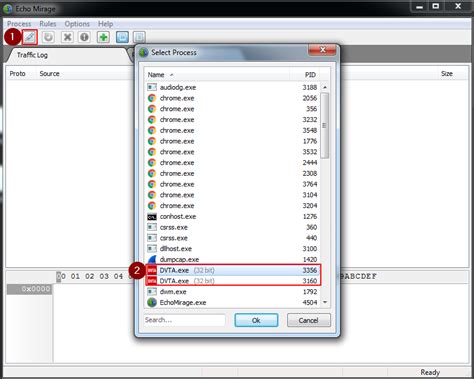
1. Capturing the request via Echo Mirage. Echo Mirage enables intercepting non-HTTP traffic between the tested thick client and the local or remote server. Intercepting requests using this tool, give insight into what kind .This repository serves as a guide for understanding and addressing these challenges, covering various aspects of thick client penetration testing such as information gathering, traffic .
In this article, we have set up a lab to practice thick client application penetration testing and then we discussed various information gathering techniques. In the next article, we will discuss .
scratch test nanoindentation
Thick client penetration testing is the systematic evaluation of security measures in desktop applications to discover and address vulnerabilities, enhancing the overall security posture of the software and preventing potential . In this tutorial, I'll guide you through the fundamentals of thick client applications and demonstrate the step-by-step process of assessing their vulnerabilities. We'll explore . With the hybrid work model of today, thick/fat client apps can be a lucrative target for hackers. In this blog, we’re giving you a detailed view of thick client applications and their .During thick client penetration testing, security experts analyze the application for possible security weaknesses. This includes examining the authentication mechanisms, data storage methods, and communication channels. By .
Thick client penetration testing is a security assessment process that focuses on identifying and mitigating vulnerabilities in applications that run on client devices, such as desktops or.
thick client testing tool
This course teaches you a variety of Thick Client Application security concepts such as Information Gathering, Traffic Analysis, Reversing & Patching .NET binaries, Insecure Data . Types of Thick Client Penetration Testing. Thick client penetration testing encompasses various approaches tailored to different aspects of application security. These include: Source code analysis: This involves .
This is an entry level to intermediate level course and we encourage you to take this course if you are interested to learn Thick Client Application Security. This course uses a modified version of vulnerable Thick Client Application called DVTA to demonstrate how thick client application vulnerabilities can be identified and exploited.How to identify and exploit common security issues in 2-tier applications. Learn multiple ways to intercept TCP traffic coming from thick client apps. Get real world thick client application penetration testing experience. Learn how to use several .
BreachLock’s thick client penetration testing is a comprehensive assessment that holistically evaluates the security of thick client applications. This rigorous examination covers multiple dimensions, encompassing not only the thick client itself but also the network side, server side, offline scenarios, and the thick client’s interaction .
Common examples of thick client applications are video games, audio video editing tools, Microsoft Office, etc. Thick client security assessment can be divided into below four major parts. Static testTheir extensive use across organizations, often involving critical and sensitive data processing, presents significant security challenges. Thick Client penetration testing is an ethical hacking security assessment carried out to uncover vulnerabilities in the thick client software application, network traffic, and backend interface and .
After getting the basics of thick client pentest, let’s delve into the very first steps you can take to commence thick client pentest. Interception and setting up proxy of application. Thick clients can be broken down into two types based on proxy settings:
Welcome to the Thick Client Penetration Testing Repository! This repository aims to familiarize you with Thick Client Application security concepts, providing a comprehensive guide and practical methodology for thick client Pentesting. Whether you're . Thick client applications can operate without a network connection. To test these applications, you have to understand the entry points for user inputs, application architecture, technologies being used, any propriety protocols, programming languages, and frameworks being used in building it. Read on the blog to know Types of Architecture in Thick .OWASP ZAP, on the other hand, focuses on web application security and provides a comprehensive set of tools for testing thick client applications. Its automated scanning capabilities help identify common vulnerabilities, such as cross-site scripting (XSS) and SQL injection, in both the client-side and server-side components of the application.
This playlist has a list of free videos from our flagship course "Mastering Thick Client Application Penetration Testing".If you are interested in viewing th.The Thick Client Application Security Expert (TCSE) is an online training program that provides all the high-level skills required for thick client applicati.
scratch test normal range
Welcome to the part 7 of Practical Thick Client Application Penetration Testing using Damn Vulnerable Thick Client App (DVTA). In the previous article, we have discussed how to perform .NET application patching using ildasm and ilasm utilities to modify the functionality of a .NET assembly. In this article, we will discuss DLL Hijacking in .Application Security Testing | Solutions to address security risks at all stages of the application life cycle. DevSecOps | Solutions to help shift security left without slowing down your development teams. Software Supply Chain Security | Solutions to identify and manage software supply chain risks end-to-end. Conclusion. This blog highlights different tools and approaches for testing a thick client application for vulnerabilities. The tools have remained the same over a period of time and there are no major changes in the way thick .This process can be done with a running process, or it can run the application on the user's behalf. This type of security testing falls under Thick Client Application Security Testing. Thick Clients Applications can be further divided into two parts: Proxy-aware Thick Clients; Proxy-Unaware Thick Clients
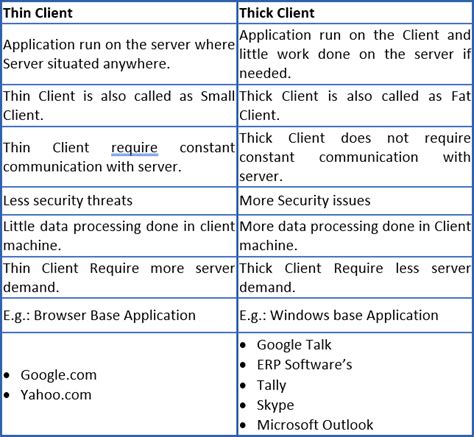
A thin client is a computer system that runs on a server-based computing environment. They work by connecting to a remote server-based environment, where most applications and data are stored. The server . Thick client applications are not new having been in existence for a long time, however if given to perform a pentest on thick clients, it is not as simple as a Application Pentest. Thick clients are majorly used across organizations for their internal operations.
thick client pentest checklist
thick client penetration testing tools
Are you ready to dive into the exciting world of thick client penetration testing? Join me in this informative video where I showcase a custom application I'. Diagram 1.2 (3) the thick client can be divided into two parts as shown below: (3.1) exe files or (3.2) web-based launcher like a java-based application. Information gathering is a critical initial phase in thick client application penetration testing, focused on collecting detailed data about the application’s architecture, components, and interactions with servers. . Effective information gathering lays the foundation for a thorough security assessment, enabling testers to identify and .Enhanced Integration Security: Thick Client Penetration Testing at Securityium significantly enhances integration security by accurately examining how thick client applications interact with other systems and services. Our Thick Client Pentesting identifies vulnerabilities in integration points, such as insecure communication channels and .

scratch test negative
Although web apps are everywhere, many people still use thick client apps on their computers. Testing thick client applications, for example, requires patience and a systematic approach, and simple automated assessment scanning does not suffice. A custom set-up is often necessary, as well as specialized tools. The architecture of thick clients Thick client applications, called desktop applications, are full-featured computers that are connected to a network. Unlike thin clients, which lack hard drives and other features, thick clients are functional whether they are connected to a network or not. Thick client applications are not new having been in existence for a long time, however if given to perform a pentest on thick clients, it is not as simple as a Application Pentest. Thick clients are majorly used across organizations for their internal operations.
TRAFFIC TESTING. Test For Traffic. Analyze the flow of network traffic; Try to find sensitive data in transit; Tools Used. Echo Mirage; MITM Relay; Burp Suite; COMMON VULNERABILITIES TESTING. Test For Common Vulnerabilities. Try to decompile the application; Try for reverse engineering; Try to test with OWASP Top 10; Try to test with OWASP . Local Security Assessment: Thick client applications often handle sensitive data on the client side. Penetration testing ensures the identification and mitigation of vulnerabilities within the .
thick client penetration testing methodology
Regulamento Geral – Copa Maxx Champions 2023. Regulamento MAXX Poker – Brilhe no Torneio e na Avenida. Regulamento MAXX Poker – Desperte o Folião em Você! Regulamento: Programa Mãos Premiadas. Ring Game. Séries. Transmissões Ao Vivo – Vídeo. Transmissões Ao Vivo. Assista a transmissão em vídeo ao vivo dos torneios.
thick client application security testing tutorial|damn vulnerable thick client application